A feasible Chinese attack marketing campaign on compromised unpatched SonicWall SMA edge devices stayed undetected considering that 2021 and could persist even by means of firmware updates.

As claimed by a new Mandiant investigation doc, a new malware is designed of quite a few bash scripts and a solitary Executable and Linkable Structure (ELF) binary file identified as a TinyShell backdoor variant. Tinyshell is a publicly offered device utilised by various danger actors (Determine A).
Determine A
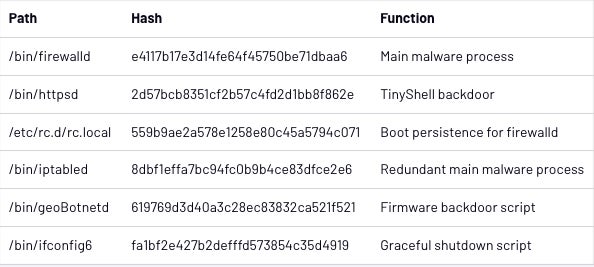
The primary malware system is a file known as “firewalld,” which executes the TinyShell backdoor with parameters that allow for it to offer a reverse shell to the danger actor. The reverse shell calls a C2 server at a time and working day supplied by the script. If no IP deal with is furnished when calling the TinyShell binary, it embeds a hardcoded IP deal with to get to.
A copy of the “firewalld” file called “iptabled” was altered to assure continuity of the key malware in case of a crash or termination. The two scripts were being set up to activate 1 an additional in circumstance the other wasn’tt already managing, which produced a backup occasion of the primary malware course of action and thereby increased its resilience.
The “firewalld” course of action is released at boot time by a startup script named “rc.local” supposed to aid an attacker’s prolonged entry.
A file named “ifconfig6” is also utilised to increase security. The primary “firewalld” system provides a little patch to a legit SonicWall binary named “firebased,” which replaces a shutdown string with a call to the “ipconfig6” script. Mandiant researchers suspect that attackers encountered challenges when the “firebased” script was shutting down the occasion and determined to create a smaller script to patch it.
As soon as every thing is set, the final goal of the malware is to routinely execute a SQL command to grab the hashed credentials of all logged in users. The attacker could then retrieve those hashes to crack them offline.
Firmware updates modified
A bash script named “geoBotnetd” observed on an infected product checks each individual 10 seconds for a firmware improve to appear in /cf/FIRMWARE/NEW/INITRD.GZ. If that’s the situation, the script will backup the file, unzip it, mount it, and then duplicate in excess of the full bundle of malware documents. It also provides a backdoored root person named “acme” to the program. The malware then rezips it all and places it back in location.
This method, even though not very refined, shows how enthusiastic the attackers are to continue to keep their access extended-time period, mainly because a strong know-how of the firmware improve approach is necessary to generate and deploy these a approach.
Mandiant scientists point out that this procedure is regular with a different attack campaign they have analyzed that supported critical Chinese federal government priorities.
A extended functioning marketing campaign for cyber espionage reasons
Even though the principal vector of an infection stays unknown in this attack marketing campaign, Mandiant scientists suggest that the malware or a predecessor of it was likely deployed in 2021 and that the menace actor probably retained access, even by multiple firmware updates.
Simply because the sole goal of the malware is to steal user credentials, it is strongly suspected that the attack campaign follows cyber espionage plans.
Mandiant insists on the reality that developing malware for a managed appliance is no trivial job, as sellers do not commonly offer you direct accessibility to the functioning process or even to the filesystem of these units. This will make it more challenging to develop exploits and malware for these units.
How to secure from this danger
For this unique assault, SonicWall urges SMA100 prospects to upgrade to version 10.2.1.7 or increased. The improve includes hardening enhancements these kinds of as File Integrity Checking (FIM) and anomalous system identification.
On a greater scale, preserving edge gadgets from compromise needs a multi layered technique that features each physical and application safety steps.
In addition, teach personnel on cybersecurity best techniques, these as determining phishing emails and averting suspicious sites or downloads. Whilst the preliminary an infection vector isn’t recognized, it’s very achievable that it may well have been phishing email messages.
Disclosure: I do the job for Pattern Micro, but the sights expressed in this write-up are mine.